JDK 14 has been released! As with my previous blogs for JDK 13 and JDK 12, I have compiled a list of what I think are the most interesting and useful security enhancements in this release. I have also grouped them into appropriate categories (crypto, TLS, etc) which should make it easier to find out what has changed in each specific area. The JDK 14 Release Notes also contain details on these and other enhancements.
Table of Contents
General
-
The deprecated
java.security.aclAPIs have been removedThese APIs were initially deprecated in Java SE 9 and marked for removal in Java SE 10. These APIs have been considered legacy for a long time. Applications should use the
java.security.Policyand related APIs instead. -
New Amazon Root CAs have been added
Four new Amazon Root Certificate Authorities (CAs) have been added to the JDK
cacertskeystore. The Distinguished Names of the CAs are:-
CN=Amazon Root CA 1, O=Amazon, C=US
-
CN=Amazon Root CA 2, O=Amazon, C=US
-
CN=Amazon Root CA 3, O=Amazon, C=US
-
CN=Amazon Root CA 4, O=Amazon, C=US
-
-
New LuxTrust Root CA has been added
One new LuxTrust Root Certificate Authority (CA) has been added to the JDK
cacertskeystore. The Distinguished Name of the CA is:- CN=LuxTrust Global Root 2, O=LuxTrust S.A., C=LU
Crypto
-
Legacy elliptic curves have been deprecated and will be removed in a future release
The implementations of 47 named elliptic curves in the
SunECprovider have been deprecated. These curves are not implemented using modern techniques and many of them are no longer recommended by standard groups. The implementations of these curves will be removed or replaced in a future release of the JDK.See the Deprecated Legacy Curves section of the JDK Providers Doc for the complete list of affected curves.
-
Legacy elliptic curves have been disabled by default in TLS, CertPath, and Signed JARs
Related to the previous issue, these curves have also been disabled by default if used in TLS protocol exchanges, certification paths, or signed JARs. A new security property named jdk.disabled.namedCurves has been added to the
java.securityconfiguration file that contains the names of the disabled curves. Certificates or protocol exchanges using these curves will be blocked or negotiated to use other acceptable curves.Below is the definition of the property in the
java.securityfile:# # This property contains a list of disabled EC Named Curves that can be included # in the jdk.[tls|certpath|jar].disabledAlgorithms properties. To include this # list in any of the disabledAlgorithms properties, add the property name as # an entry. jdk.disabled.namedCurves = secp112r1, secp112r2, secp128r1, secp128r2, \ secp160k1, secp160r1, secp160r2, secp192k1, secp192r1, secp224k1, \ secp224r1, secp256k1, sect113r1, sect113r2, sect131r1, sect131r2, \ sect163k1, sect163r1, sect163r2, sect193r1, sect193r2, sect233k1, \ sect233r1, sect239k1, sect283k1, sect283r1, sect409k1, sect409r1, \ sect571k1, sect571r1, X9.62 c2tnb191v1, X9.62 c2tnb191v2, \ X9.62 c2tnb191v3, X9.62 c2tnb239v1, X9.62 c2tnb239v2, X9.62 c2tnb239v3, \ X9.62 c2tnb359v1, X9.62 c2tnb431r1, X9.62 prime192v2, X9.62 prime192v3, \ X9.62 prime239v1, X9.62 prime239v2, X9.62 prime239v3, brainpoolP256r1, \ brainpoolP320r1, brainpoolP384r1, brainpoolP512r1 -
The
OracleUCryptoprovider has been deprecated for removalThe
OracleUCryptoprovider is supported only on the Solaris platform and provides access to the algorithms in the native Solaris Ucrypto cryptographic library. It has been deprecated as part of JEP 362 (Deprecate the Solaris SPARC Ports). The provider will be removed from a future JDK release when the Solaris ports are officially removed.
TLS
-
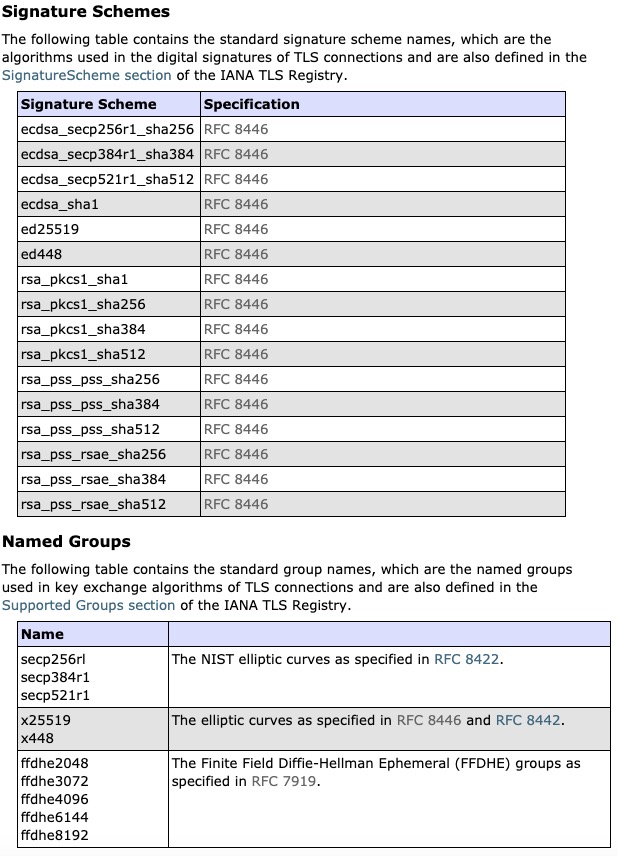
Standard Names for Signature Schemes and Named Groups defined
Standard names have been defined for TLS signature schemes and named groups in the Standard Algorithm Names Specification. This improves compatibility by providing standard names for signature schemes and elliptic curves which can be specified by applications in various APIs and properties.
Below is a snapshot of the names from the Signature Schemes and Named Groups sections of the Java Security Standard Algorithm Names specification.
-
SSLv2HelloandSSLv3have been removed from the default enabled TLS protocolsAs a further strengthening measure,
SSLv2HelloandSSLv3have been removed from the default list of enabled TLS protocols. Note thatSSLv3had already been restricted by default as it is included in thejdk.tls.disabledAlgorithmssecurity property in the system-widejava.securityconfiguration file. With this change,SSLv3is not enabled by default even if it is removed from thejdk.tls.disabledAlgorithmssecurity property.
XML Signature
-
XML Signature implementation updated to Apache Santuario v2.1.4
The XML Signature implementation in the JDK has been updated to version 2.1.4 of Apache Santuario XML Security for Java, which it is based on.
With this update, one new system property has been added:
com.sun.org.apache.xml.internal.security.parser.pool-size. This can be set to the pool size of the internalDocumentBuildercache used to process XML Signatures. The default value is 20. Setting this property may improve performance depending on the application’s use case.
Tools
-
The default algorithms for
keytool -keyalghave been removedKey algorithm defaults are no longer supported and
keytoolnow exits with an error if a specific algorithm is not specified using the-keyalgoption when generating keys with the-genkeypairor-genseckeycommands.Here is an example output of running the command:
$ keytool -genkeypair Enter keystore password: keytool error: java.lang.Exception: The -keyalg option must be specified.