JDK 19 was released on September 20, 2022! As with my previous blogs, I have compiled a list of what I think are the most interesting and useful security enhancements in this release. I have also grouped them into appropriate categories (crypto, PKI, etc) which should make it easier to find out what has changed in each specific area. The JDK 19 release notes also contain further details on these and other enhancements.
Highlights of this release include further improvements that strengthen the default security of the Java Platform and improved TLS performance. There are also several other really useful enhancements such as adding KeyStore support for accessing local machine certificates on Windows and support for TLS channel binding tokens with HTTPS and Kerberos.
Table of Contents
Crypto
-
Default key sizes increased
The default sizes for keys generated by JDK implementations of
KeyPairGeneratorandKeyGeneratorhave been increased as follows:- For the “RSA”, “RSASSA-PSS”, and “DH” algorithms, the default size has been increased from 2048 bits to 3072 bits
- For the “EC” algorithm, the default size has been increased from 256 bits to 384 bits
- For the “AES” algorithm, the default size has been increased from 128 bits to 256 bits (if permitted by crypto policy), otherwise the default falls back to 128 bits
Issue: JDK-8267319
-
SHA3 performance increased up to 2x
The JDK “SUN” provider SHA3 message digest algorithm performance has been increased up to 2x.
Issue: JDK-8275914
-
OAEPParameterSpec.DEFAULT is deprecated
The
DEFAULTstatic field of thejavax.crypto.spec.OAEPParameterSpecclass has been deprecated. This constant uses default algorithms such as SHA-1 that have weakened. Applications should avoid using this constant and explicitly specify the parameters using theOAEPParameterSpec(String, String, AlgorithmParameterSpec, PSource)constructor.Issue: JDK-8284553
-
PSSParameterSpec(int) and PSSParameterSpec.DEFAULT are deprecated
The
PSSParameterSpec(int)constructor andDEFAULTstatic field have been deprecated. This constructor and constant uses SHA-1 as the default hash algorithm which has weakened and is no longer recommended. Applications should avoid using this constructor or constant and explicitly specify the parameters using thePSSParameterSpec(String, String, AlgorithmParameterSpec, int, int)constructor.
PKI
-
New Windows KeyStore types for accessing local machine certificates
Two additional
KeyStoretypes have been added, “Windows-MY-LOCALMACHINE” and “Windows-ROOT-LOCALMACHINE”, which provide access to keys and certificates stored on the Windows Operating System that are available to all accounts.The other Windows
KeyStoretypes, “Windows-MY” and “Windows-ROOT” provide access to keys and certificates associated with the current user’s account only. To avoid confusion, new names for these types have also been introduced, “Windows-MY-CURRENTUSER” and “Windows-ROOT-CURRENTUSER” which map to “Windows-MY” and “Windows-ROOT”, respectively.The new
KeyStoretypes are documented in the SunMSCAPI Provider section of the JDK Providers Guide.Issue: JDK-6782021
-
Enhanced support for OtherNames in X.509 certificates
The JDK implementation of the
getSubjectAlternativeNamesand thegetIssuerAlternativeNamesmethods of theX509CertificateAPI have been enhanced to return more useful information for OtherName types. The returned list now has a 3rd and 4th entry which contain the OID (as a String) and the ASN.1 encoded value (as a String if it is a character string, otherwise a byte array). These additional values can help applications to more easily identify what type the OtherName is, and avoid additional parsing of the encoded value to determine the OID and value.Issue: JDK-8277976
TLS
-
TLS performance related improvements
Several performance related improvements have been made which speedup and reduce the amount of memory used during a TLS handshake. See the following issues for more details:
-
3DES suites removed from default enabled TLS cipher suites
3DES cipher suites have been removed from the default enabled TLS cipher suites. Note that these cipher suites were already disabled since “3DES” is included in the
jdk.tls.disabledAlgorithmssecurity property and by default the suites will not be considered for a TLS connection handshake.This change makes it much harder to enable 3DES cipher suites either accidentally or maliciously. Per RFC 7525, implementations SHOULD NOT negotiate cipher suites that use algorithms offering less than 128 bits of security. The strength of 3DES is 112 bits, which is less than 128 bits of security.
We don’t recommend re-enabling the suites, but the release note contains instructions for doing that, if necessary.
Issue: JDK-8163327
-
New APIs for customizing TLS and DTLS signature schemes
Two new APIs have been added which allow applications to customize and retrieve the prioritized list of signature schemes used when negotiating a TLS or DTLS connection:
javax.net.ssl.SSLParameters::setSignatureSchemesandjavax.net.ssl.SSLParameters::getSignatureSchemes.Issue: JDK-8280494
-
RFC 6125 endpoint identification algorithm fully supported
RFC 6125 defines procedures for verifying identities in TLS certificates. The JDK implementation was mostly compliant except for one case which has now been corrected: the implementation will not attempt to match wildcard domains in TLS certificates where the wildcard character comprises a label other than the left-most label (ex: we won’t match “foo.*.example.net”).
If necessary, applications can workaround this restriction by implementing their own
HostnameVerifierorTrustManager.Issue: JDK-7192189
-
New SSLException constructors that take cause as a parameter
New constructors have been added to the
SSLHandshakeException,SSLKeyException,SSLPeerUnverifiedException, andSSLProtocolExceptionAPIs that take a cause (Throwable) as a parameter. This provides a more convenient option than having to separately call theinitCausemethod.Issue: JDK-8282723
Tools
-
Default digest and signature algorithms strengthened for jarsigner
The default digest and signature algorithms used by
jarsignerwhen signing JAR files have been strengthened.The default digest algorithm has been changed from SHA-256 to SHA-384.
The default signature algorithm for RSA and RSASSA-PSS keys greater than or equal to 624 bits has been changed from SHA256withRSA to SHA384withRSA, except for keys greater than 7680 bits where SHA512withRSA is used. Similarly, the default signature algorithm for EC keys has been changed from SHA256withECDSA to SHA384withECDSA, except for keys greater than or equal to 512 bits where SHA512withECDSA is used.
Here is the complete table of signature algorithm defaults from the
jarsignertool specification: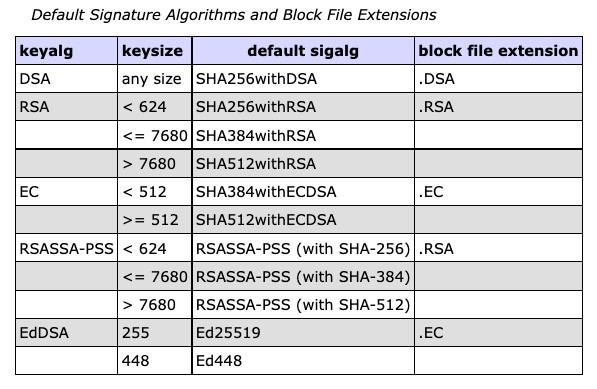
Issue: JDK-8267319
-
RC2 and RC4 added to jdk.security.legacyAlgorithms security property
“RC2” and “ARCFOUR” (RC4) have been added to the
jdk.security.legacyAlgorithmssecurity property in thejava.securityconfiguration file. Keys using these algorithms are no longer recommended.keytoolwill now emit warnings if keys of this algorithm are used in any commands associated with secret key entries of a keystore. Here is an example:
$ keytool -genseckey -keyalg RC2 -keysize 128 -keystore keystore Enter keystore password: Generated 128-bit RC2 secret key Warning: The generated secret key uses the RC2 algorithm which is considered a security risk.
Issue: JDK-8286090
-
DES, DESede, and MD5 added to jdk.security.legacyAlgorithms security property
“DES”, “DESede” (3DES) and “MD5” have been added to the
jdk.security.legacyAlgorithmssecurity property in thejava.securityconfiguration file. Keys using these algorithms are no longer recommended.keytoolwill now emit warnings if keys or certificates use any of these algorithms. Here is an example:
$ keytool -genseckey -keyalg DES -keystore keystore Enter keystore password: Generated 56-bit DES secret key Warning: The generated secret key uses the DES algorithm which is considered a security risk.
Issue: JDK-8255552
-
New jarsigner -providerPath option
A new
-providerPathoption has been added to thejarsignertool. This option allows the user to specify the class path of an alternate keystore implementation and can be used in conjunction with the-providerClassoption. Here is an example:
$ jarsigner -keystore keystore -storetype MYKS -providerPath mods/test.myks \ -providerClass org.test.MyProvider signed.jar mykey Enter keystore password: jar signed.
Issue: JDK-8281175
-
New Kerberos ktab options for providing salt values
Two new options have been added to the Windows
ktabtool to allow users to provide alternate salt values when using the-aoption to generate keys. These salt values are used instead of using the default salt which is a concatenation of the realm and username. The-s <salt>option allows the user to provide their own salt, and the-foption will fetch the salt from the KDC. These options are useful if the KDC uses a different salt value, or the user simply wants to use a different salt value.Issue: JDK-8279064
Networking
Two other important JDK 19 security related enhancements in the networking area that provide significant security benefits and are worth mentioning are:
-
HTTPS Channel Binding support for Java GSS/Kerberos
This enhancement adds support for TLS channel binding for Negotiate/Kerberos authentication over HTTPS through
javax.net.HttpsURLConnection.A new system property named
jdk.https.negotiate.cbthas been introduced to allow users to configure how channel binding tokens are used byHttpsURLConnection.See the release note for more details.
Issue: JDK-8279842
-
Disable http DIGEST mechanism with MD5 and SHA-1 by default
The MD5 and SHA-1 HTTP DIGEST mechanisms have been disabled by default. These algorithms have weaknesses and are no longer recommended.
A new system property named
http.auth.digest.reEnabledAlgorithmshas been introduced which can be used to re-enable these mechanisms, if necessary, and at your own risk.Issue: JDK-8281561